Project details
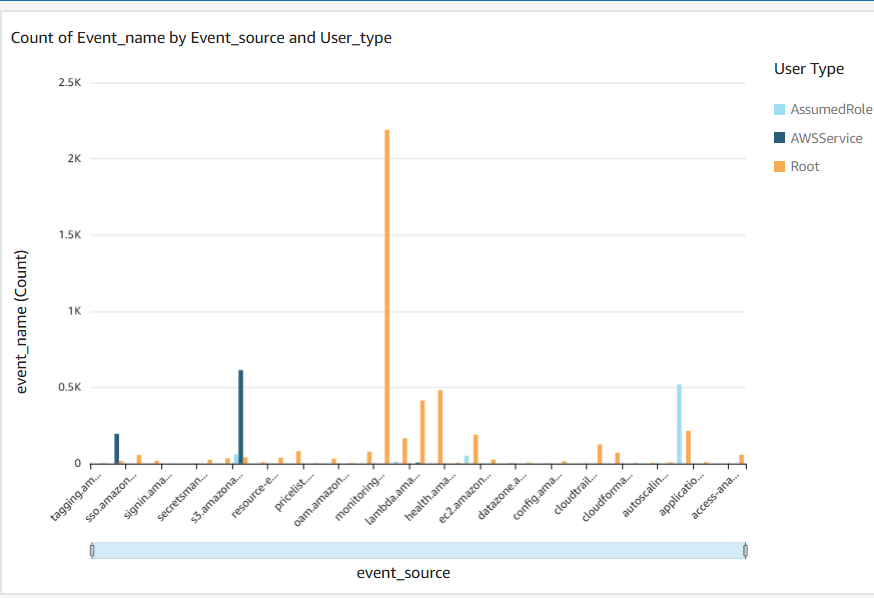
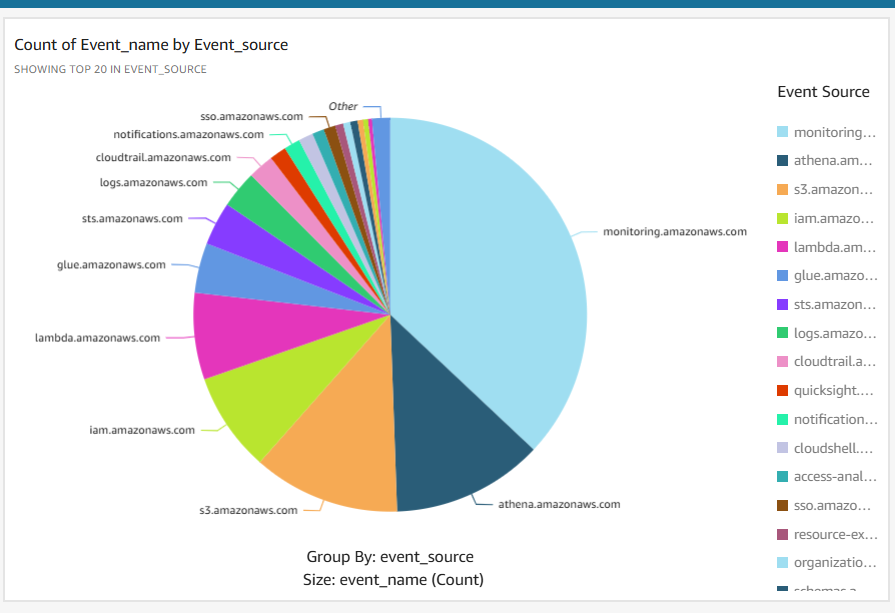
AWS Secret Monitoring
This project establishes real-time monitoring for AWS Secrets Manager access, triggering immediate alerts via Slack/Teams for suspicious activity like IAM Role usage or anomalous access patterns. It leverages CloudTrail, CloudWatch, Lambda, and SNS to provide enhanced security visibility into sensitive data access.
Project Components & Uses:
✅ Secret Access Logging (CloudTrail + S3)
Captures all GetSecretValue API calls for auditing.
✅ Real-time Monitoring & Filtering (CloudWatch Logs + Metric Filters)
Analyzes logs instantly to count general vs. IAM Role access.
✅ Anomaly Detection Alerting (CloudWatch Alarms)
Flags unusual deviations from normal secret access patterns.
✅ IAM Role Access Alerting (CloudWatch Alarms)
Triggers immediate alerts specifically for role-based access.
✅ AI-driven Event Summarization (AWS Bedrock + Lambda)
Generates concise, human-readable summaries of access events.
✅ Automated Secret Rotation (Lambda)
Automatically changes secrets if accessed from untrusted IPs (Hardening Step).
✅ Slack/Teams Integration (SNS + Lambda)
Delivers real-time alerts and summaries to communication channels.
✅ Historical Log Analysis & Reporting (Athena + Glue Data Catalog)
Enables SQL querying of raw CloudTrail logs stored in S3.
✅ Interactive Security Dashboards (QuickSight)
Visualizes access trends, user activity, and source IPs.